Hari Iyer | SyncEzy
CEO4 Min Read
Jun 26, 2023
Late Friday evening on 23rd June, as I was shutting down for the day, at 6.15 pm I received a concerned email from a customer in Singapore, Is SyncEzy protected against this Zero Day Exploit?
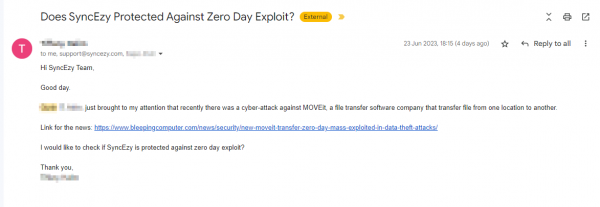
This by the way is a perfect subject to get any TECH CEO to open the email immediately. As I opened the email carefully checking the link and the sender details to see if I was not being phished at the same time. I saw the email was genuine from our customer and the attack being referred to was a serious exploit in the MOVEit Transfer, tracked as CVE-2023-34362.
This particular breach was a stark reminder that even established managed file transfer (MFT) platforms backed by Huge Publicly listed companies can fall prey to threat actors. With Progress Corporation, the parent company of MOVEit Transfer, scrambling to patch the issue and secure their software, it’s time to take a step back and understand how SyncEzy is redefining the standards for data transfer security.
Fortunately due to some wise decisions on our part we were not impacted and are likely to be insulated from these kinds of threats.
Auth 2.0 Industry Standard
In this digital era, it’s crucial to use tried-and-true measures to secure data. SyncEzy leverages the Auth 2.0 industry standard for authorization, a robust protocol that allows applications to obtain limited access to user accounts on HTTP services such as Microsoft, Office 365, Procore, simPRO, and Google. By using Auth 2.0, SyncEzy ensures that only authorized personnel have access to sensitive data, thereby significantly reducing potential security risk

Reduced Attack Surface
At SyncEzy, we’re committed to minimizing the attack surface. For most of our integrations, like all the Procore integrations. We only store metadata in our database, ensuring that any potential data breach does not result in the loss of sensitive information. This approach also provides an additional layer of protection against mass data downloads similar to those seen in the recent MOVEit breach. It reduces the attack surface and the value we hold.
No Local Data Storage
We further secure your data by not storing any of it locally with SyncEzy. Without local data, the possibility of data theft via local attacks is eliminated. This approach also negates the risks associated with physical storage loss or theft.
Restricted URL Access
Security doesn’t stop at storage. We’ve implemented a system where customer data can only be accessed from restricted URLs. This feature, in combination with our use of Auth 2.0, makes it exceptionally difficult for potential hackers to gain unauthorized access to sensitive information.
No Local Installation Required
One of the key differentiators between SyncEzy and other MFT solutions lies in our approach to application deployment. With SyncEzy, there’s no need for any local installation of our application. This aspect has a twofold advantage. First, it bypasses the need to expose network vulnerabilities or to open up network ports, which can often be a gateway for threat actors. This drastically reduces the risk of an attacker exploiting a zero-day vulnerability, as was the case in the recent MOVEit Transfer attack. Second, it ensures that our solution is always up to date, with the latest security patches and performance enhancements, since everything is handled at the server level.

Soc2 Type 2 Certification
To ensure we maintain the highest standards of security, SyncEzy has secured a Soc2 Type 2 certification. This certification is not easily obtained; it involves extensive audits and proves our commitment to managing customer data securely. It confirms that SyncEzy has the necessary measures in place to protect your data against unauthorized access and system failures.
In conclusion, while the MOVEit Transfer breach is an unfortunate incident, it serves as a timely reminder of the need for robust security in data transfer solutions. Despite its stature as an award-winning and publicly traded company on the stock exchange, Progress Corporation’s recent cyber-attack underlines the reality that even the most robust and reputed organizations are not impervious to the sophisticated threats in today’s digital landscape.
At SyncEzy, we are committed to continually evolving our security measures to safeguard your data effectively and efficiently. Our use of the Auth 2.0 industry standard, restricted URL access, a no-local-storage policy, and our SOC2 Type 2 certification all combine to ensure your data is in safe hands.
In a world where data is becoming increasingly valuable, make sure your Data Transfer and Sync solution is secure. Choose SyncEzy for data transfers you can trust.